Microsoft Enterprise Mobility + Security (EMS) is excited to deliver conditional access protection for Microsoft Edge on iOS and Android. This integration expands your management capabilities as you deploy Microsoft Edge for the best browsing experience across all endpoints in the enterprise. Microsoft Edge on iOS and Android with conditional access gives users easy, secure access to Office 365 and all your web apps that use Azure Active Directory, with the same application management and security capabilities that previously required Intune Managed Browser.
We are excited to share the following capabilities are now in public preview for Microsoft Edge on iOS and Android:
- Microsoft Edge single sign-on (SSO): Your employees can enjoy single sign-on across native clients (such as Microsoft Outlook) and Microsoft Edge for all Azure Active Directory connected apps.
- Microsoft Edge conditional access: You can now require employees to use Microsoft Intune protected browsers such as Microsoft Edge using application-based conditional access policies.
Let's dive a little deeper to explore these new features
Single Sign-on to Azure AD-connected apps in Microsoft Edge
Microsoft Edge on iOS and Android can now take advantage of single sign-on (SSO) to all web apps (SaaS and on-premises) that are Azure AD-connected. This means users of Microsoft Edge will be able to access Azure AD-connected web apps without having to re-enter their credentials. They simply need to have the Microsoft Authenticator app on iOS or the Intune Company Portal app on Android.
Let’s see how users can get this better sign-in experience on iOS devices:
- Install the latest version of Microsoft Edge. If you don’t have Microsoft Authenticator installed yet, you will be prompted to download it.Image may be NSFW.
Clik here to view.
- Sign-in and navigate to any of your Azure AD-connected applications that support single sign-on. You will be prompted to register your device, and that's it you will receive single sign-on access to all applications.
Image may be NSFW.
Clik here to view.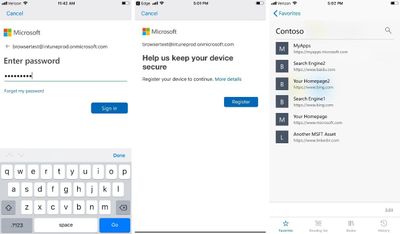
If you previously used Intune Managed Browser with Azure AD Conditional Access, this new Microsoft Edge functionality will be familiar to you. Now, users protected with device-based conditional access can navigate to all links using Microsoft Edge from Outlook mobile, and access web resources without having to reauthenticate. To enable this, users only need to set Microsoft Edge as their default browser in their Outlook app settings.
Image may be NSFW.
Clik here to view. Set default browser in Outlook settings
Set default browser in Outlook settings
Secure mobile browser access using Conditional Access and Microsoft Edge
You can now enforce policy-managed Microsoft Edge as the approved mobile browser to access Azure AD-connected web apps, restricting the use of unprotected browsers like Safari or Chrome. This allows you to secure access and prevent data leakage via unprotected browser applications. A similar protection can be applied to Office 365 services like Exchange Online and SharePoint Online, the Office portal, and access to on-premises (intranet) sites via the Azure AD Application Proxy.
Users attempting to use unmanaged browsers such as Safari and Chrome will be prompted to open Microsoft Edge instead. On first attempt, users will be prompted to install the Microsoft Authenticator on iOS or the Intune Company Portal on Android. Here is a screenshot of a blocked access when using Safari on iOS.
Image may be NSFW.
Clik here to view.
To configure this in Microsoft Intune, you need to apply application-based conditional access policy and an App Protection policy for Microsoft Edge on iOS and Android. Here’s how you do that:
Create a conditional access policy to lock down browser access to a policy-protected browser such as Microsoft Edge using app-based conditional access. Here’s a screenshot of a policy targeting browser access.Image may be NSFW.
Clik here to view.
You may then select the control to grant access to cloud resources only from approved clients apps that can protect your corporate data. Image may be NSFW.
Clik here to view.
Create an Intune application protection policy and target all users for the Microsoft Edge application. This screenshot shows how to target Microsoft Edge.
Image may be NSFW.
Clik here to view.
In addition to conditional access and single sign-on, here are other features and benefits enjoyed by users of Microsoft Edge managed and protected by Microsoft EMS:
- Dual-Identity: Microsoft Edge now supports corporate and personal work identities. There is complete separation between the two identities, like the architecture and experience of Outlook and Office 365. Users can seamlessly transition between work and personal identities while corporate content is kept secured.
- Configuration settings: Admins can configure a homepage shortcut, bookmarks, MyApps integration, Azure app proxy, allow and block URL lists, and more for Microsoft Edge.
- Fast page-rendering: Consumers already love Microsoft Edge, and one thing we hear over and over is that they love how fast it is.
- Rich set of personalization and productivity features: Microsoft Edge comes with modern features such as seamless browsing across mobile and desktop, Voice Search, a built-in QR code reader, syncing capabilities to keep users’ eBooks, passwords, and favorites shared across devices. Learn more about the first-class features built into Microsoft Edge here.
Go ahead and download Microsoft Edge to experience these benefits today. Here’s a set of quick links to get you started:
- How to use Azure AD Application Proxy
- Authoring conditional access policy
- App-based conditional access technical documentation
- App protection policies in Intune
- Configure Microsoft Edge policies in Intune
As always, we’d love to hear any feedback or suggestions you have. Just email us here and let us know what you think!
Follow @MSIntune @AzureAD and @MicrosoftEdge on Twitter
(This post is authored in collaboration with Microsoft Intune, Azure Active Directory and Microsoft Edge product experts)
